When the crime scene is a computer: How Virginia Tech’s IT Security Office uses forensics to solve cyber incidents

Your inbox notification dings. It’s an email from your department head. The wording is a little odd, but they’re asking you to review a document as soon as possible, so you open the attachment to check it out, and are immediately filled with a chilling regret. The attachment is clearly not from your department head. Have you been hacked?
When cybersecurity incidents such as the one in this scenario occur at Virginia Tech, the IT Security Office (ITSO) is ready to help. The ITSO, a unit of the Division of Information Technology, is home to several computer forensics specialists who are trained to investigate cybersecurity incidents at the university.
“Security is a back and forth between bad actors and defenders,” said Jeff Lang, director of cyber defense operations for the ITSO. “Attackers constantly change their tactics and techniques to bypass the protections we have in place. During our forensic investigations, our goal is not only to figure out how they performed the attack, but also how to identify and protect against it in the future.”
What is computer forensics?
Forensics is the scientific process used to collect and analyze evidence during a criminal investigation and provide evidence that can be used in prosecuting a case. Computer forensics involves extracting electronically stored data to determine if sensitive data has been accessed or stolen and, if so, by whom.
The methodology is similar to traditional forensics work, only the tools are different. Beth Lancaster, an IT security analyst for the ITSO, elaborated, “computer forensics can be host-based or network-based. Host-based forensics looks at specific machines or files to find suspicious information, malware, or other digital artifacts.” She likens this to performing an autopsy to determine the exact cause of death (i.e., the “when and what” of the incident).
“Network forensics allows us to analyze traffic surrounding an incident,” said Lancaster. “We can collect evidence, such as websites that were visited, if and when remote access was granted, and whether any data was taken out of the network.” This part of the job is similar to taking pictures of a crime scene to establish a timeline and piece together the actions surrounding the incident.
Both types of forensics work require highly specialized skills — and plenty of patience, added Lang.
“It’s a common misconception that computer forensics work can be done very quickly — that we bang out a few keystrokes and we’ve solved the case, like what’s portrayed on TV. In reality, it’s a very time-consuming process. It can take many days to complete an investigative analysis, even with the most capable analysts on the case,” said Lang.
How does the computer forensics process work at Virginia Tech?
In most cases, the ITSO will begin forensics work at the request of a university official, a department, or the Virginia Tech Police Department following a confirmed or suspected incident. The ITSO cooperates with the involved parties to perform forensic analysis that can help identify where, when, and how a breach occurred, as well as what data was compromised.
“When dealing with a possible threat, our goal is to prevent further intrusions; limit the possible damage of an intrusion; and facilitate recovery of data, functionality, and security after an intrusion with minimal downtime,” explained Lang. “Along the way, we collect and analyze information into evidence that shows what happened, how it happened, and why it happened.”
Lang pointed out that many of the same skills used in forensics work are used to proactively analyze network traffic to determine if suspicious activity is taking place. “This process is called cyberthreat hunting and accounts for a significant amount of the work we do in the ITSO.”
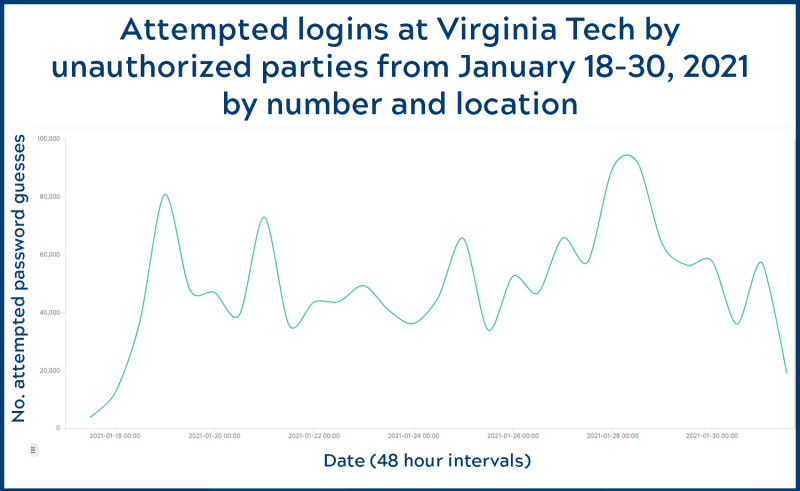
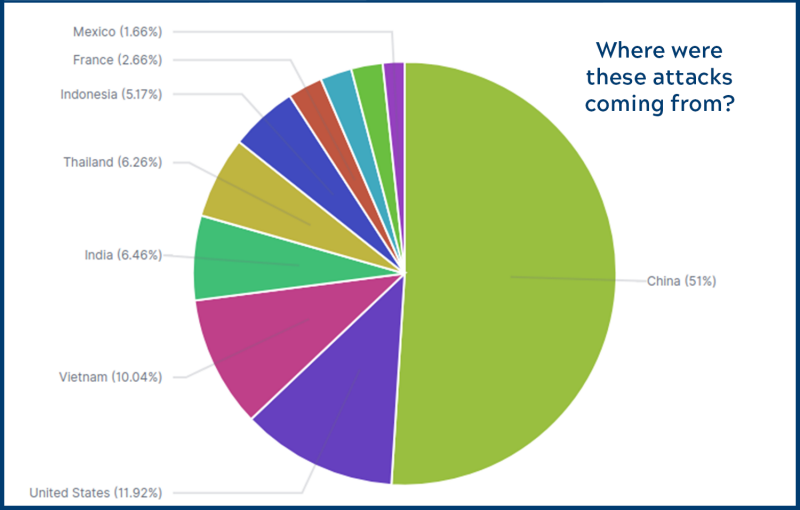
By analyzing and neutralizing threats before they occur, while responding rapidly to all reported incidents, the ITSO is not only protecting Virginia Tech’s data systems, but also its infrastructure from falling prey to potentially dangerous attacks. As the recent breach of a Florida water treatment plant control system reminds us, cybersecurity measures protect much more than computers.
How not to be at the center of a computer forensics investigation
One thing the ITSO team unanimously agrees upon is that preventing bad actors from making it too far onto your systems or devices is better than mitigating the aftereffects of an intrusion.
“Every day we detect traffic that is scanning our network for devices, attempting to log into machines, and testing web servers for vulnerabilities,” said Randy Marchany, Virginia Tech’s university IT security officer. “While our defense operations thwart most data exposure threats, individual users need to do their part to protect themselves.” He offers the following advice:
- Use strong passwords that meet or exceed Virginia Tech’s rules.
- Use a unique password for each account, so that if one password is stolen, the damage is limited to one account and much easier to fix. A password manager app can be useful to help keep track of account logins.
- Always use 2-factor authentication whenever it is an option; this adds a second layer of security to your accounts.
- Learn how to identify phishing scams. This guide offers helpful advice for identifying and reporting suspicious emails. The ITSO also offers interactive phishing awareness training for departments to improve their employees’ ability to detect phishing attempts.
- Trust your gut. If something seems “off” about a website, video, email, or text message, it probably is. “When in doubt, report it,” said Marchany.
If you suspect your VT account or university-owned equipment has been hacked, follow these instructions to report the incident. The ITSO will evaluate the accounts and/or systems in question and help you safely regain access to your accounts. For personal devices or nonuniversity networks, he recommends reporting to the appropriate vendor.

For more information about the IT Security Office at Virginia Tech, visit security.vt.edu. For computer or IT support at Virginia Tech, visit 4help.vt.edu.